Antminer S17/T17 Support
Antminer S17/T17 Support
Check out a new firmware based on the original firmware plus built-in hive client.
Links in the description https://github.com/minershive/hiveos-asic
You can install the firmware both through the web interface and through btc tools.
After installing the firmware, you can enter farm_hash in the web interface on the HiveOS tab. Or install the archive with farm_hash in bulk using btc tools or the web interface.
Generate the archive using this link: http://download.hiveos.farm/asic/repo/farm_hash/
Deprecated manual:
Content
- For S17 / S17 Pro start from step 1
- For T17 start from step 2
1. Update to the official firmware released on May 27th.
If the firmware is older than the official released on May 24th, you’ll need to update to that one first(Stage 1).
If the firmware is the official released on May 24th, you can update from Stage 2. Download the firmware from the official website, or follow the links below:
Stage 1
| Device | Firmware |
|---|---|
| S17 | Antminer-S17-user-MD-201905241706-sig.tar.gz |
| S17 Pro | Antminer-S17Pro-user-MD-201905241708-sig.tar.gz |
Stage 2
| Device | Firmware |
|---|---|
| S17 | Antminer-S17-user-OM-201905271110-sig.tar.gz |
| S17 Pro | Antminer-S17Pro-user-OM-201905271111-sig.tar.gz |
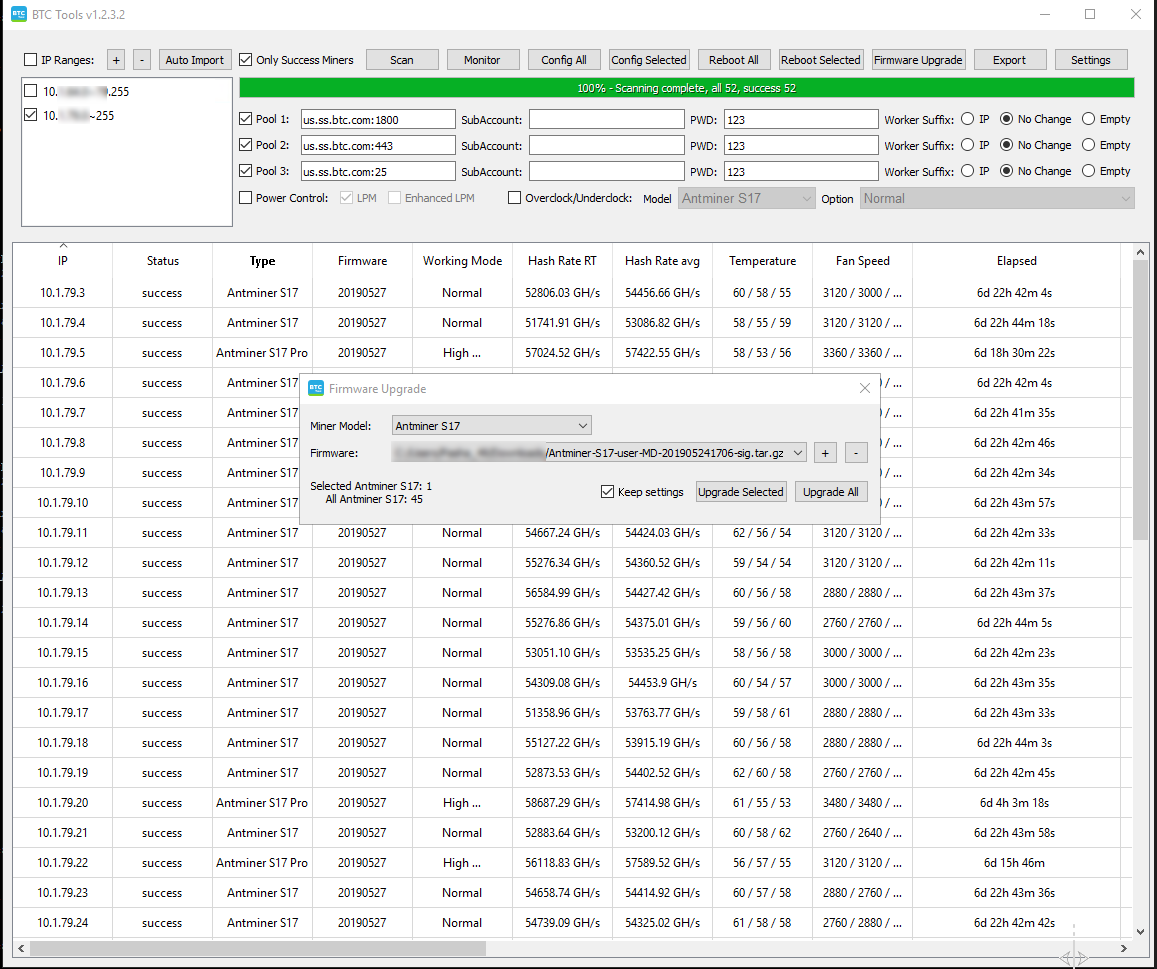
IIf there are only a few devices, you can update them via the web interface. If there is a large number of devices, we advise updating via BTC-tools for Windows: Download | Manual
Enter the desired network rage to scan, locate and select the desired devices, click on Firmware Upgrade, and select the downloaded firmware file.
Additional instructions for T17/S17/S17 Pro
2. Download bulk install scripts:
apt-get install -y sshpass curl
cd /tmp && curl -L --insecure -s -O https://raw.githubusercontent.com/minershive/hiveos-asic/master/hive/hive-asic-net-installer/download.sh && sh download.sh
cd /tmp/hive-bulk-install
3. Download ssh unlock script:
wget http://download.hiveos.farm/antminerssshinst/ssh.sh
chmod +x ssh.sh
4. Scan the network to compile a list of ASICs IPs (example):
./ipscan.sh 192.168.1.0/24 10.0.1.0/24 > ips.txt
You can add a filter to narrow the list down in case there are different models on the same network (optional):
./ipscan_model.sh "S17 Pro" или ./ipscan_model.sh "T17"
This will create a list into file S17.txt. Rename it:
mv S17.txt ips.txt
5. Unlock ssh.
./ssh.sh
After unlocking, devices will be rebooted. After executing the script, wait about 5 minutes for ssh to reboot and start.
6. Download firmware script, and flash the device:
wget http://download.hiveos.farm/antminerssshinst/S17T17.sh
chmod +x S17T17.sh
If there aren’t many devices, and you don’t mind the higher network load, run:
./S17T17.sh
ASICs download firmware, about 23 MB of traffic per device.
If there are a large number of devices or you need to be cautious about the network load, you can add the “local” parameter:
./S17T17.sh local
The firmware is downloaded to the folder with the scripts and uploaded by SCP on the ASICs. The firmware is downloaded sequentially, to avoid network overload and thus, minimizing network related errors. The firmware is automatically flashed in the background, without requiring any user response.
7. Register ASICs with FARM_HASH
Add the FARM_HASH to the config.txt file and execute the script:
/.setup.sh
P.S. 1
If you reset the ASIC settings by pressing the reset button, ssh access will be lost and the Hive configs will be lost.However, hive scripts will remain. You will need to repeat step 5 and 7
P.S. 2
Bitmain’s latest firmware, along with improving mining stability, added bugs in the web interface. In particular, breaking the update via the web interface. Updating to newer firmware in the future via the web does not work, but can be updated via ssh. Although we would be able to fix this, it may cause issues if they release firmware updates with fixes for this vulnerability and clients start to update via the web, they will be unable install Hive.
P.S. 3
This installation method opens SSH on the devices. Open SSH with a standard password is not secure leaving devices exposed, which can lead to numerous issues. Currently, there are no recovery images available for SD Card Recovery, and you will have to physically recover via UART.
It is recommended to change the SSH password by executing the passwd command.
Another option is to close SSH by sending the rm /config/dropbear command via hive and rebooting the ASIC.
The web interface vulnerability still remains, and it is thereforem, recommended to change the web password via the device’s web-interface.
 Поддержка Antminer S17/T17/T15 в HiveOS
Поддержка Antminer S17/T17/T15 в HiveOS